A wireless body area network (WBAN) connects independent nodes that are placed in the clothes, on the body or under the skin of a person. The network expands over the whole human body and the nodes are connected through a wireless communication channel.
The IEEE 802.15.6 Standard defines a communication standard optimized for miniaturised low-power devices that are deployed on or implanted inside a human body for a variety of medical, non-medical and entertainment applications.
In medical application, WBAN allows remote health monitoring of a patient over periods of time without any restriction to his activities. Vital information of a patient is collected and continually forwarded to a remote monitoring station for further analysis. WBAN can also be used to help people with disability.
Non-medical applications include monitoring forgotten things, data file transfer, gaming and social networking.
The Physical Layer
The frequencies for WBANs are regulated by communication authorities in different countries. The Medical Implant Communications Service (MICS) band is a licensed band used for implant communications and has the same frequency range of 402–405MHz in most countries. Wireless Medical Telemetry Services (WMTS) is a licensed band used for medical telemetry systems. However, the MICS and WMTS bands are unable to support high data rate applications.The Industrial, Scientific, and Medical (ISM) and Ultra-wideband (UWB) bands are able to support high data rate applications and are available worldwide. Unfortunately, there is a high probability of interference because many wireless devices operate in the 2.4GHz band.
The standard defines three PHY layers (one is optional), which is selected depending on the application requirements.
- Narrowband PHY (NB) is optional. It is responsible for activation/deactvation of the radio transceiver, clear channel assessment (CCA) and data transmission/reception. The Physical Protocol Data Unit (PPDU) contains the PLCP preamble, PLCP header, and a Physical Service Data Unit (PSDU).
IEEE 802.15.6 Modulation Parameters IEEE 802.15.6 NB PPDU Structure PLCP preamble helps the receiver with the timing synchronization and carrier-offset frequency. The PLCP header contains information for successful decoding of a packet by the receiver. The PSDU contains a MAC header, MAC frame body and FCS.
A WBAN device should be able to support transmission and reception in one of the frequency bands shown in the table above.
- Ultra wideband PHY (UWB) is mandatory. It operates in two frequency bands, i.e., low band and high band. Each band is divided into channels with a bandwidth of 499.2 MHz. The low band consists of 3 channels (1-3). Channel 2 is mandatory and has a central frequency of 3993.6 MHz. The high band consists of 8 channels (4-11). channel 7 is mandatory and has a central frequency of 7987.s MHz. Other channels are optional. The UWB PHY transceivers allow low implementation complexity.
IEEE 802.15.6 UWB PPDU Structure The UWB PPDU contains a synchronization header (SHR), PHY header (PHR) and PSDU. The SHR contains a preamble and a start frame delimiter (SFD). The PHR contains information about the data rate of the PSDU, payload length and scrambler seed. The receiver usesd the information in the PHR to decode the PSDU.
The data rate is between 0.5 Mbps to 10 Mbps with 0.4882 Mbps as the mandatory rate.
- Human body communication PHY (HBC) is mandatory. It operates in two frequency bands centered at 16 MHz and 27 MHz with a bandwidth of 4 MHz. Both operating bands are valid for USA, Japan and Korea. The 27 MHZ band is valid for Europe. HBC is the electrostatic field Communication (EFC) PHY specification.
IEEE 802.15.6 EFC PPDU Structure The PPDU consists of a preamble, SFD, PHY header and PSDU. The preamble and SFD are fixed data patterns, which are pre-generated and sent ahead of the packet header and payload. The preamble sequence is transmitted four times to ensure packet synchronization. The SFD is transmitted once.
When the receiver receives the packet, it finds the start of the packet by detecting the preamble sequence. Then it finds the start of the frame by detecting SFD.
The MAC Layer
Nodes are organised into one- or two-hop star topology. One hub / coordinator controls the operation of the network. A WBAN consists of one hub and a number of nodes, between zero to MaxBANSize.The MAC protocol controls access to the channel. The hub divides the channel into a series of superframes, which are bounded by beacon periods of equal length. The hub may shift the offsets of the beacon period.
Each superframe contains allocation slots that are used for data transmission. The slots have equal duration and are numbered from 0 to 𝑠, where 𝑠 ≤ 255. The hub transmits beacons to define the superframe boundaries and allocate the slots.
For non-beacon modes, the superframe boundaries are defined by polling frames.
The MAC frame consists of a 56-bit header, variable length frame body (max 255 bytes), and 16-bit FCS.
The MAC header consists of a 32-bit frame control, 8-bit recipient Identification (ID), 8-bit sender ID, and 8-bit WBAN ID fields. The WBAN ID contains information on the WBAN in which the transmission is active.
The frame control field contains control information, i.e., the type of frame (e.g., beacon, acknowledgement, or other control frames). The first 8-bit field in the MAC frame body contains message freshness information required for nonce construction and replay detection. The last 32-bit Message Integrity Code (MIC) authenticates and verifies the integrity of the frame.
The IEEE 802.15.6 network operates in one of the following modes:
- Beacon mode with beacon period superframe boundaries. The beacons are transmitted by the hub in each beacon period except in inactive superframes or unless prohibited by regulations. The superframe structure is divided into Exclusive Access Phase 1 (EAP1), Random Access Phase 1 (RAP1), Type I/II phase, Exclusive Access Phase 2 (EAP 2), Random Access Phase 2 (RAP 2), Type I/II phase, and a Contention Access Phase (CAP).
In EAP, RAP and CAP periods, nodes contend for the resource allocation using either CSMA/CA or a Slotted Aloha access procedure. EAP1 and EAP2 are used for highest priority traffic, such as reporting emergency events. The RAP1, RAP2, and CAP are used for regular traffic.
Type I/II phases are used for uplink allocation intervals, downlink allocation intervals, bi-link allocation intervals, and delay bi-link allocation intervals. Polling is used for resource allocation. Depending on the requirements, the hub can disable any of these periods by setting the duration length to zero.
- Non-beacon mode with superframe boundaries. The entire superframe duration is covered either by a Type I or a Type II access phase, never both.
- Non-beacon mode without superframe boundaries. The coordinator provides unscheduled Type II polled
allocation only.
The access mechanisms used in each period of the superframe are divided into three categories:
- Random access mechanism that uses either CSMA/CA or a slotted Aloha procedure for resource allocation,
- Improvised and unscheduled access (connectionless contention-free access that uses unscheduled polling/posting for resource allocation,
- Scheduled access and variants (connection-oriented contention-free access) that schedules the slot allocation in one or multiple upcoming superframes (also called 1-periodic or m-periodic allocations).
IEEE 802.15.6 CSMA/CA Procedure In CSMA/CA, a node sets its backoff counter to a random integer number uniformly distributed over the interval [1, CW], where CW ∈ (CWmin, CWmax). The value of CWmin and CWmax vary depending on the user priority.
The node decrements the backoff counter by one for each idle CSMA slot of duration equal to pCSMASlotLength. The data is transmitted when the backoff counter reaches zero. The CW is doubled for each failure until it reaches CWmax.
In RAP1, the node first waits for SIFS = pSIFS duration, and then decrements the backoff counter until it reaches zero, where the data transmission starts. In CAP, the node locks the backoff counter because the time between the end of the slot and the end of the CAP is not enough for completing data transmission and a Nominal Guard Time represented by GTn. The backoff counter is unlocked in the next RAP2 period.
Security Specification
There are three security levels:- Level 0: unsecured communication. Data is transmitted in unsecured frames with no data authentication, integrity check, confidentiality and privacy protection, and replay defense.
- Level 1: authentication only. Transmitted data is authentication but not encrypted. No confidentiality and privacy support.
- Level 2: authentication and encryption. Data is transmitted in secured, authenticated and encrypted frames.
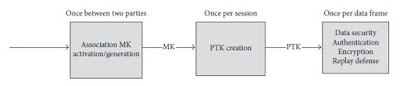
The security level is selected during the association process. A Master Key (MK) is activated for unicast secured communication. The MK may be pre-shared or established using unauthenticated association. Then, a Pairwise Temporal Key (PTK) is created for one session. For multicast secured communication, a Group Temporal Key (GTK) is shared with the corresponding group using the unicast method.
The security protocols are based on the Diffie-Hellman key exchange. The private keys used in the association and disassociation processes are unique 256-bit integers. The Cipher-based Message Authentication Code (CMAC) is used to derive the Key Message Authentication Codes (KMAC) and MK. Initially, the node and hub have a pre-shared MK, which is used for the security association procedure.
The node initiates the process by sending a security association frame request to the hub. The hub responds by either joining or aborting the association. If the node receives an abort message, it stops the association procedure. If the node receives a joining response, the pre-shared MK is activated and shared between the node and hub upon mutual agreement, which is then used to generate a PTK.
The disassociation procedure can be initiated either by the node or hub. The sender sends a security disassociation frame request and then removes the MK and corresponding PTK from its storage. When the recipient receives the request, it also removes the key from its storage.
Source
- K.S. Kwak, S. Ullah, N. Ullah (2010). An overview of IEEE 802.15.6 standard , Proc. of the 2010 3rd International Symposium on Applied Sciences in Biomedical and Communication Technologies (ISABEL 2010), 7-10 Nov. 2010, Rome, Italy
- S. Ullah, M. Mohaisen, M.A. Alnuem (2013). A Review of IEEE 802.15.6 MAC, PHY, and Security Specifications, International Journal of Distributed Sensor Networks, Volume 2013















Absolutely loved this post! Your perspective is refreshing and incredibly informative. Thank you for sharing your knowledge. Eagerly awaiting your next update!
ReplyDeleteRF Communication Units
Enrgtech